Physical security devices were not designed to protect the new virtual components architecture of virtualization. Such “traditional” security depends on physical devices deployed on the perimeter of the data center or on physical networks. These physical devices depend on network inspection and are thus blind to the significant security-related activity within virtual infrastructure, whose networks they cannot see.
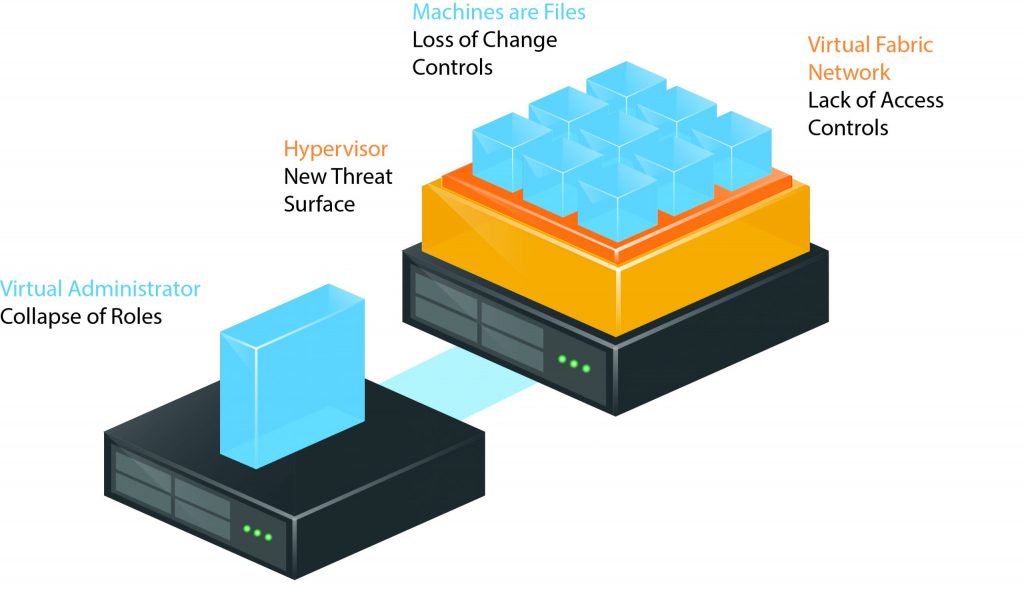
Virtualization brings four significant changes to security:
- A new virtual network fabric, blind to physical security devices
- A new threat surface: the hypervisor
- An all-powerful virtual administrator, collapsing roles
- Machines becoming files, leading to mobility, rapid change and opportunity for theft
Each of these changes brings unique security challenges.
Security professionals need to recognize what is new and adapt their security practices to accommodate. If not, virtualization will pose a significant security risk. Indeed, in recognition of these changes, independent 3rd party standards bodies, such as PCI and NIST, have modified their own regulations. Their updated specifications acknowledge that without appropriate technology and training, virtualization and cloud systems will introduce significant security and compliance gaps. Such gaps include unprotected networks, access control failures, loss of change controls, new threat surfaces, breakdowns in separation of duties and escalation of privilege. Virtualization security addresses these potential gaps while also reducing cost and complexity.
I am text block. Click edit button to change this text. Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.



